How to Generate an SSH Public or Private Key
Using a public or private key to authenticate when logging into SSH can provide convenience or security. The public or private key is a secure alternative to password login. No username/password is required to connect to the server via SSH. Instead, the unique public and private keys provide secure authentication. You're advised to use a key password that's different from your cPanel password.
Difference Between Public and Private SSH Keys
Your public key is stored on the server, while your private key is stored locally on your computer or server. When accessing a server, your computer's private key is compared to the server's public key. If the two match, you'll be granted remote access to the server.
How to Generate SSH Keys in cPanel
Generate the Public SSH Key
- Log in to your Bluehost Portal.
- Click Hosting in the left-hand menu.
- In the hosting details page, click the cPanel button.
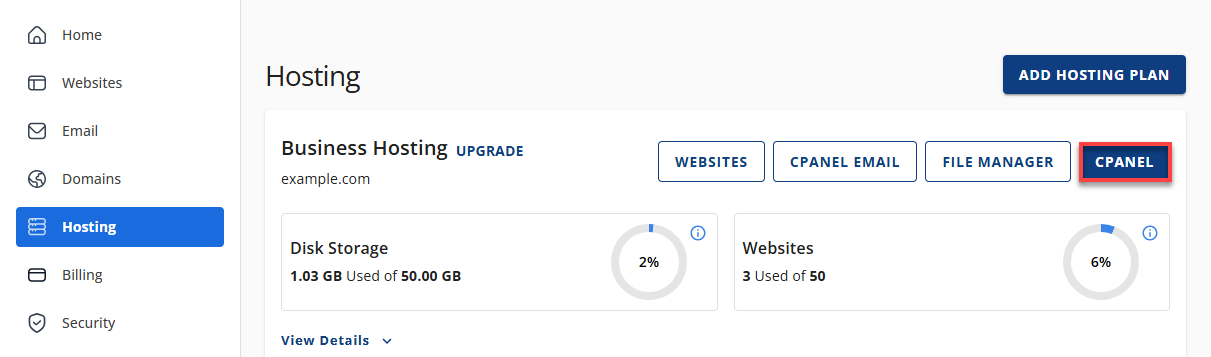
- Your cPanel will open in a new tab.
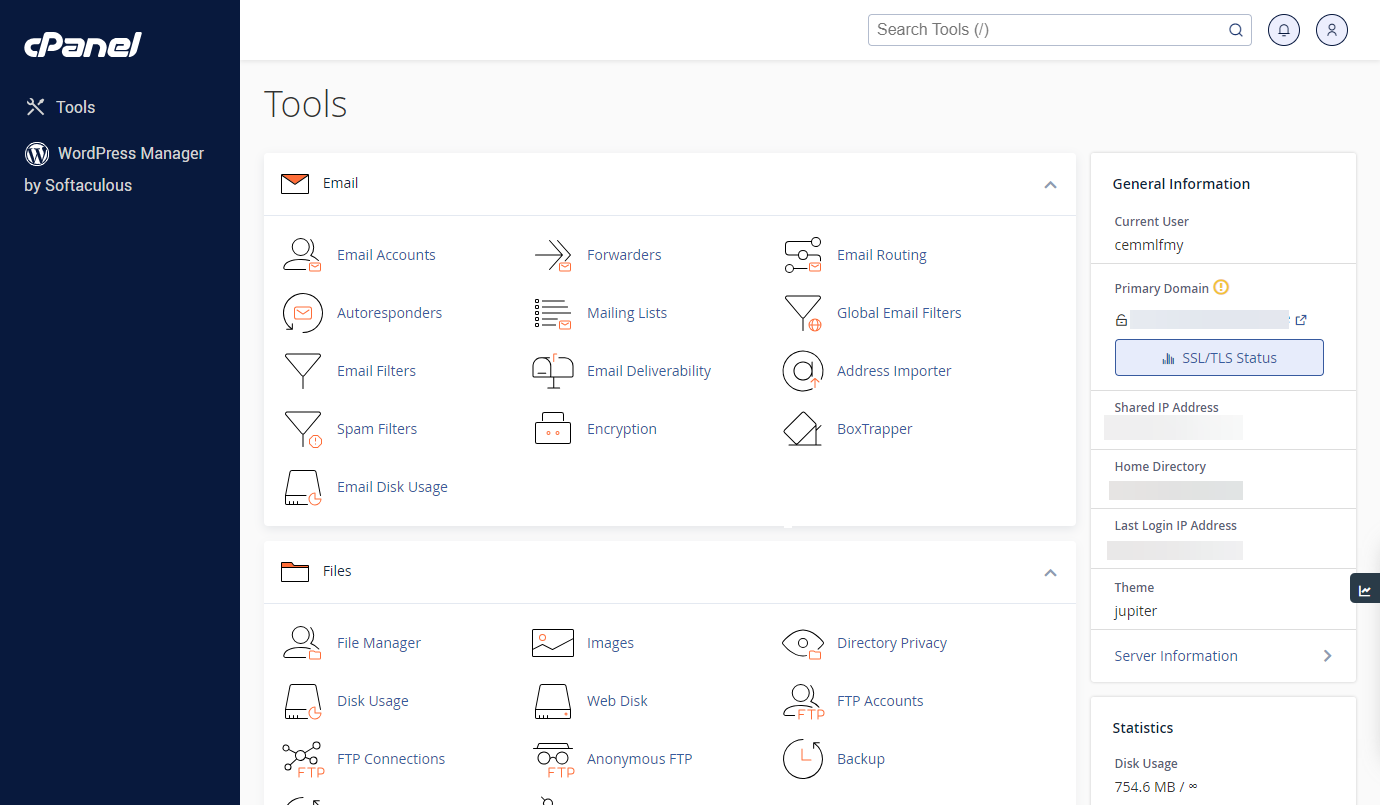
- Select SSH Access under the Security category.
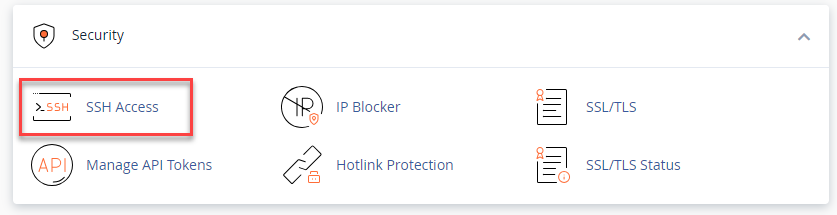
- From the Manage SSH Keys page, click Generate a New Key.
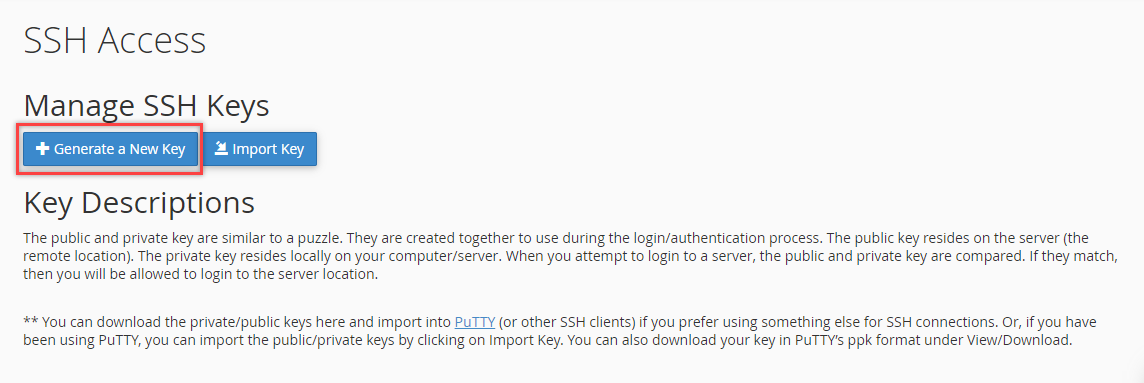
- Enter a new Key password, then ensure that you type it again under the Reenter Password field.
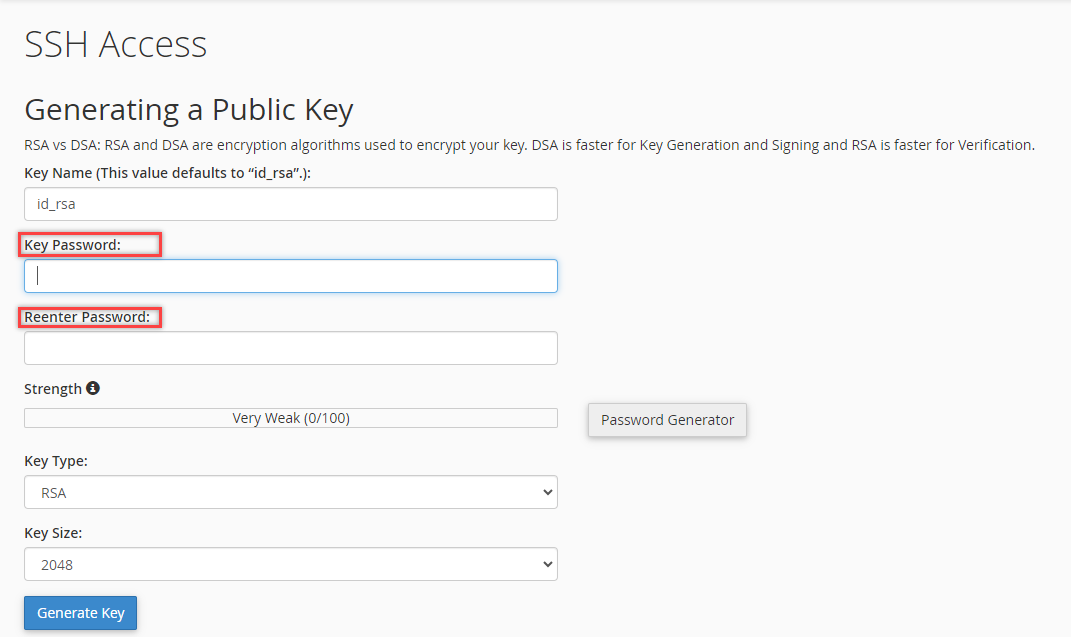
- Choose DSA or RSA for the type.
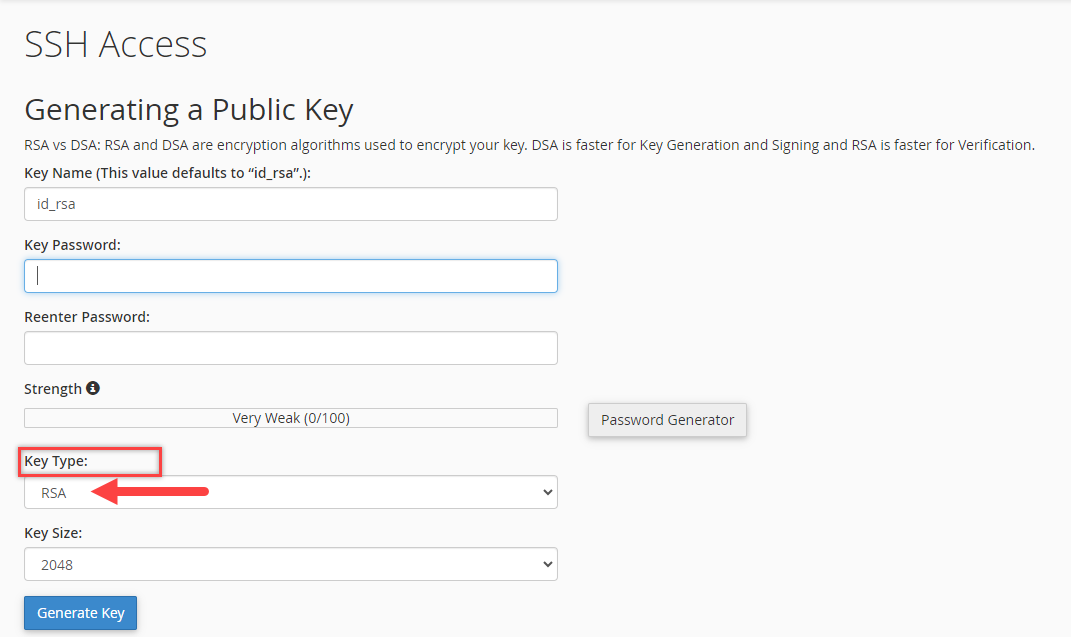
It's recommended that you choose the RSA SSH key. Note that DSA keys provide quicker key generation and signing times, while RSA keys provide quicker verification times. - Choose a Key size. It's recommended to use 2048 or higher.
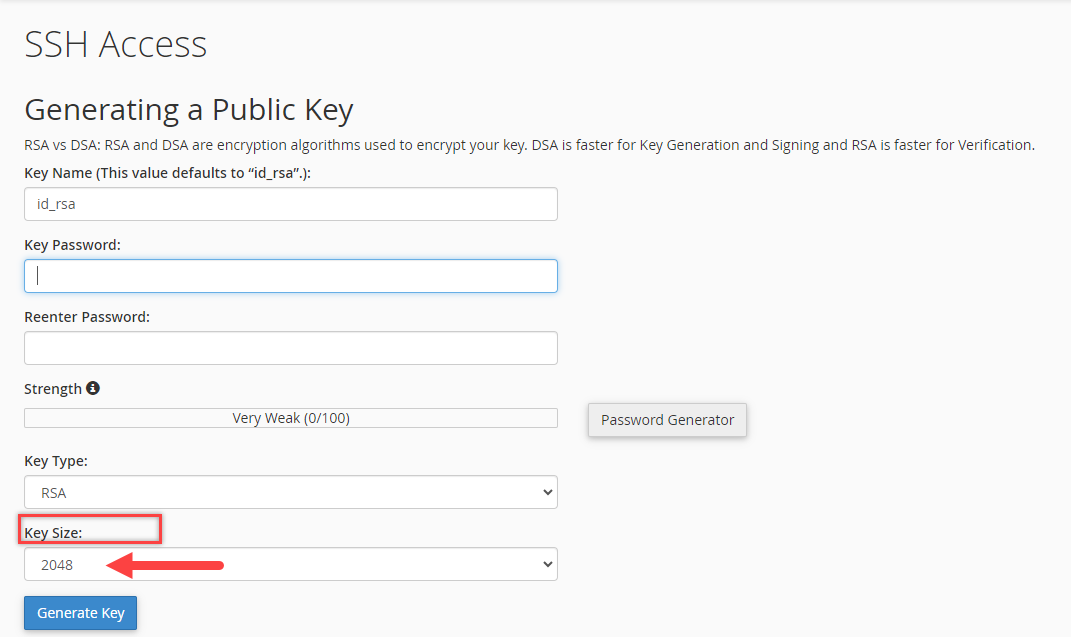
- Click Generate Key.
- Click the Go Back button.
Authorize the Public Key
Authorizing the key will add the public key to the authorized_keys file.
- Click Manage from the Public Keys section for the key you want to authorize.
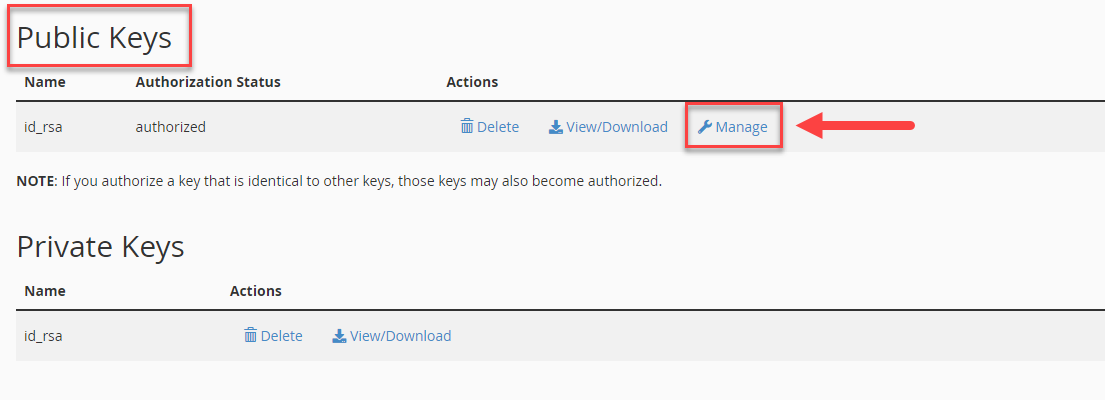
- Click the Authorize button for your newly created key.
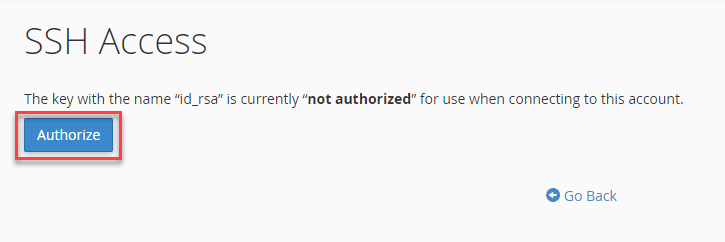
- Click Go Back to return to the main page.
View or Download the Private Key
The private key needs to be stored on your local computer.
- To the right of your private key, click View/Download.
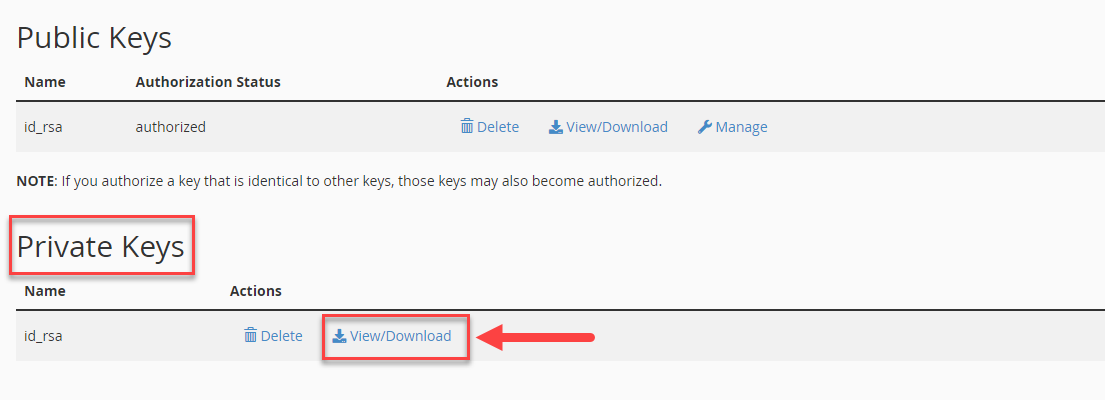
- Click the Download Key button to download the private key.
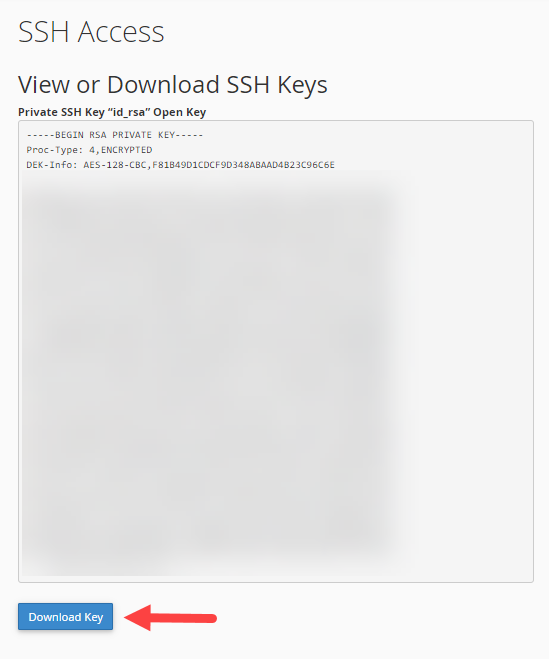
- If on Linux or Mac OS, copy the id_dsa file to your ~/.ssh folder.
- On Windows, you'll want to move it someplace safe.
How to Connect to Your Server Using SSH
Windows
To log in to your server with PuTTY and a public key, please see Using SSH on Windows (PuTTY) for step-by-step instructions.
Linux or MacOS
To log in to your server with a password using macOS or Linux, follow these steps:
- Open your Terminal.
- Enter the following command. Replace port with the port number, ssh-key with the file path, and IP with your IP address.
ssh -p port -i ssh-key user@IP - Enter the passphrase for the key.
Using a passphrase with your SSH key is important because it prevents unauthorized access by individuals who don't have the passphrase. Without a passphrase, anyone accessing your computer could copy your private key.
'~/.ssh/id_dsa':
After entering the passphrase, you'll be connected to the server.
Best Practices for SSH Key Management
Maintaining the security of SSH keys is essential for safeguarding access to your systems. Follow these best practices to mitigate the risk of unauthorized access and ensure the integrity of your infrastructure:
- Use strong passphrases: Always protect your private keys with strong, complex passphrases. This ensures that even if a key is compromised, you'll still be able to prevent unauthorized access.
- Regularly rotate keys: Implement a policy for the regular rotation of SSH keys to minimize the risk of exposure. Change the keys periodically to help maintain the security of your connections.
- Encrypt private keys: Store private keys using strong encryption on your disk. Encryption acts as a second line of defense against unauthorized access. This safeguards your keys even if your system is compromised.
- Disable password authentication: Switch off password-based authentication on your servers and rely solely on key-based authentication. This significantly reduces the risk of brute-force attacks.
- Monitor key usage: Set up monitoring and logging for SSH key usage to quickly detect and respond to suspicious activities. This helps identify potential security breaches early.
- Educate users on security practices: Educate all users about the risks of mishandling SSH keys and promote a culture of security awareness. Training should cover proper handling, storage, and usage of SSH keys.
- Audit SSH key access. Regularly audit your SSH keys and access rights to ensure that only authorized keys are used and that you comply with your organization's security policies. Remove any obsolete or unauthorized keys promptly.
Summary
Our guide takes you through the steps to generate your own SSH public and private key, authorize it, and view or download the private key. Moreover, we've got instructions for connecting to your server using SSH on Windows, macOS, or Linux. By using SSH keys, you can ensure a secure login process.
If you need further assistance, feel free to contact us via Chat or Phone:
- Chat Support - While on our website, you should see a CHAT bubble in the bottom right-hand corner of the page. Click anywhere on the bubble to begin a chat session.
- Phone Support -
- US: 888-401-4678
- International: +1 801-765-9400
You may also refer to our Knowledge Base articles to help answer common questions and guide you through various setup, configuration, and troubleshooting steps.