Key highlights
- Access your server securely and manage it directly from the command line.
- Navigate directories, view and manage files efficiently.
- Execute commands for SSH remotely and automate tasks quickly.
- Transfer files safely using SCP, SFTP or rsync.
- Enhance security with SSH keys, custom ports and restricted access.
Managing a server doesn’t have to mean navigating complex dashboards or clicking through multiple menus. SSH (Secure Shell) provides secure, direct access to your server, commonly Linux. This allows you to execute commands, transfer files and troubleshoot issues instantly.
From deploying websites and optimizing performance to automating tasks and managing applications, SSH gives full control over your Linux server environment. Its command-line interface may seem intimidating at first. But mastering a few essential commands can dramatically speed up workflows and unlock capabilities that a standard control panel cannot offer.
This guide covers the most practical SSH commands with clear examples, helping you work efficiently, troubleshoot effectively and manage servers with confidence.
Quick SSH commands overview
Before diving into detailed commands for SSH, here’s a quick overview of the most essential commands you’ll use to connect, navigate, manage files and monitor your server.
| Category | Command | Purpose |
|---|---|---|
| Connecting to server | ssh username@server_ip | Connect to a server securely |
ssh username@server_ip -p PORT | Connect using a custom port | |
ssh username@server_ip 'command' | Run a command remotely without opening full session | |
| Navigation | pwd | Show current directory |
ls / ls -al | List files and folders | |
cd /path | Change directory | |
| File management | touch filename | Create a new file |
cat filename | View full file contents | |
less filename | Scroll through file contents | |
cp source destination | Copy files or directories (-r for directories) | |
mv oldname newname | Move or rename files | |
rm filename | Delete files (-r for directories) | |
| Searching files | grep "text" filename | Search for text inside a file |
find /path -name "filename" | Locate files by name | |
head filename | View first few lines of a file | |
tail filename | View last few lines / live logs | |
| Processes & system | ps aux | Show running processes |
top | Real-time system monitoring | |
kill PID | Terminate a process | |
df -h | Check disk space | |
du -sh foldername | Check folder size | |
| File transfer | scp file.txt username@server_ip:/path | Copy files to/from server |
sftp username@server_ip | Interactive file transfer session | |
rsync -av file.txt username@server_ip:/path | Sync files efficiently | |
| SSH options | ssh -i ~/.ssh/id_rsa username@server_ip | Use specific private key |
ssh -v username@server_ip | Enable verbose output | |
ssh -L local_port:localhost:remote_port username@server_ip | Forward ports | |
| SSH keys | ssh-keygen | SSH key generation pair |
ssh-copy-id username@server_ip | Copy public key to server |
As we dive deeper into SSH, these commands will become second nature, helping you manage your server efficiently and securely.
What is SSH and why is it important?
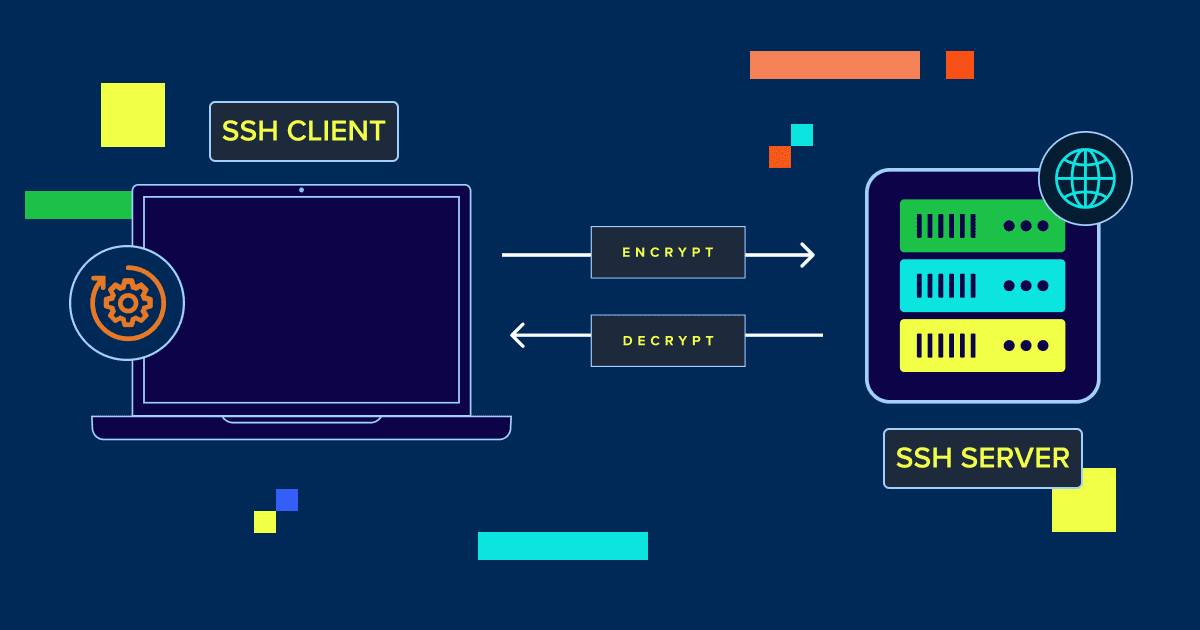
SSH or Secure Shell, is a protocol that lets you connect to a remote server safely. Think of it as a secure tunnel between your computer and the Linux server, where all communication is encrypted. This means your passwords, files and commands stay protected, even over public networks.
It’s important because it gives you direct control over your server. You can transfer and manage files, install software, monitor performance and troubleshoot issues – all without relying on a web-based dashboard. From developers to website owners, SSH is the tool that makes server management faster, safer and more efficient.
Now that we know how important SSH is, let’s understand how you can connect Secure Shell commands to your Linux server.
Connecting to a server using SSH
Before you can manage a server, you need to connect to it securely. SSH (Secure Shell) provides an encrypted connection, letting you run commands and manage files as if you were working directly on the server.
The basic SSH command is simple:
ssh username@server_ip
Here, username is your server account and server_ip is the Linux server’s address. This opens a secure terminal session where you can navigate directories, manage files and execute commands for SSH.
Basic SSH command syntax
This syntax forms the foundation for all SSH operations. You just type the command, provide your username and specify the server address to connect.
1. Connecting with username and IP
For example, to connect to a Linux server using the account admin at IP 192.168.1.10, you’d use:
ssh [email protected]
Once connected, you can perform tasks like editing files, checking logs and running scripts directly on the Linux server.
2. Using a custom port
If the server uses a non-standard port, you can specify it with -p followed by the port number:
ssh [email protected] -p 2222
This ensures your SSH connection goes through the correct port while staying secure.
3. Running commands remotely
You can also execute a single command on the server without opening a full session. For instance:
ssh [email protected] 'ls -al /var/www'
This is useful for automating tasks, quickly checking files or running scripts without staying logged in.
By understanding these basics, you can securely access your server and start managing files, directories and applications efficiently. With basics clear, it’s time to understand various SSH commands – from basic advance commands.
Basic navigation commands
Once you are connected to a Linux server, the first thing you will do is move around the file system. Linux navigation commands help you understand where you are and what files exist.
1. Print working directory (pwd)
The pwd command shows your current directory. It helps you confirm your location inside the server.
pwd
This is useful when working inside large folder structures or scripts.
2. List files and folders (ls)
The ls command displays files and directories in the current location.
ls
You can add flags for more details. For example, ls -al shows hidden files and permissions.
3. Change directory (cd)
The cd command moves you between directories.
cd /var/www
Use cd .. to go back one level. Use cd ~ to return to your home directory.
These basic commands make it easy to explore the server and find the files you need.
File management commands
After navigating the file system, you’ll often need to create, view, move or delete files. These commands help you manage files directly from the terminal.
1. Create files (touch)
The touch command creates a new empty file. It can also update the timestamp of an existing file.
touch example.txt
This is useful for creating configuration files or placeholders quickly.
2. View file contents (cat, less)
The cat command displays the full contents of a file.
cat example.txt
For long files, less is more practical. It lets you scroll through content one screen at a time.
less example.txt
3. Copy files (cp)
The cp command copies files from one location to another.
cp file1.txt file2.txtYou can also copy directories using cp -r.
4. Move or rename files (mv)
The mv command moves files or renames them.
mv oldname.txt newname.txtIt works the same way for moving files into another directory.
Delete files (rm)The rm command deletes files permanently. Use it with care.
rm example.txtTo remove directories, use rm -r. Always double-check before running delete commands.
Searching and viewing files
As your Linux server fills with files, finding the right content becomes important. These commands help you search text, locate files and preview content quickly.
1. Search text in files (grep)
The grep command searches for specific text inside files. It’s useful for scanning logs and configuration files.
grep "error" logfile.txt
This command finds every line that contains the word “error.”
2. Find files (find)
The find command locates files and directories by name, type or size.
find /var/www -name "config.php"
This searches for a file named config.php inside the specified directory.
3. View file start and end (head, tail)
The head command shows the first few lines of a file.
head logfile.txt
The tail command shows the last few lines. It’s useful for watching live logs.
tail logfile.txt
These SSH commands help you locate files and inspect content without opening large files fully.
Process and system commands
Once your server is running, you may need to monitor performance and control running programs. These commands help you understand what is happening on your system.
1. View running processes (ps)
The ps command shows a snapshot of active processes. It helps you identify what programs are currently running.
ps aux
This output includes process IDs, resource usage and the command being executed.
2. Live system monitoring (top)
The top command displays real-time system activity. It updates continuously and shows CPU and memory usage.
top
This is useful for spotting performance issues or high resource consumption.
3. Kill a process (kill)
The kill command stops a running process using its process ID.
kill 1234
Use this when an application becomes unresponsive or misbehaves.
4. Check disk space (df, du)
The df command shows available disk space.
df -h
The du command shows how much space files and directories use.
du -sh foldername
These commands help you monitor system health and prevent storage issues.
File transfer over SSH
Moving files between your computer and a Linux server is a common task. SSH provides secure tools to transfer data without exposing it to the public internet.
1. Copy files using SCP
The scp command copies files between local and remote systems. It uses SSH encryption for secure transfers.
scp file.txt username@server_ip:/home/username/
This uploads file.txt to the specified directory on the Linux server.
2. Transfer files using SFTP
Secure FTP provides an interactive file transfer session over SSH. It works like a command-line file manager.
sftp username@server_ip
Once connected, you can upload, download and list files using simple commands.
3. Sync files using rsync
The rsync command syncs files efficiently between systems. It only transfers changes, saving time and bandwidth.
rsync -av file.txt username@server_ip:/home/username/
This is ideal for backups, deployments and large file transfers.
Useful SSH options
SSH includes several options that make connections more flexible and easier to troubleshoot. These flags help you customize how SSH behaves during a session.
1. Use an identity file (-i)
The -i option lets you specify a private key file for authentication. This is useful when managing multiple servers or key pairs.
ssh -i ~/.ssh/id_rsa username@server_ip
This tells SSH which key to use for the connection.
2. Enable verbose mode (-v)
The -v option enables verbose output. It shows detailed connection logs and authentication steps.
ssh -v username@server_ip
This helps diagnose connection issues and configuration errors.
3. Forward ports (-L, -R)
Port forwarding allows secure access to services running on a remote server.
ssh -L 8080:localhost:80 username@server_ip
This forwards local port 8080 to port 80 on the Linux server. It’s useful for testing web apps securely.
SSH key commands
SSH keys provide a more secure way to authenticate without entering a password each time. They are widely used for automation and long-term server access and management.
1. Generate SSH keys (ssh-keygen)
The ssh-keygen command creates a public and private key pair.
ssh-keygen
Follow the prompts to choose a file location and optional passphrase. This generates two files: a private key and a public key.
2. Copy keys to a Linux server (ssh-copy-id)
The ssh-copy-id command adds your public key to a server’s authorized keys file.
ssh-copy-id username@server_ip
This allows passwordless login using your private key. It improves security and simplifies future connections. Besides this, using other tips is essential to ensure your website’s security.
Security best practices while using SSH
Securing SSH is critical for protecting your Linux server from unauthorized access. Implementing a few key practices can greatly reduce risks and keep your server safe.
Disable root login 1.
Direct root access should be disabled in your SSH configuration. This prevents attackers from targeting the highest-privilege account directly.
Use strong SSH keys 2.
Use modern, strong key pairs for authentication. Protect private keys with passphrases and never share or store them publicly.
Implement firewalls and restrict access 3.
Limit SSH access to trusted IP addresses or networks. This minimizes exposure to unknown sources and automated attacks.
Enable two-factor authentication (2FA) 4.
Add an extra layer of security by requiring both a password and a temporary code when logging in. You can also use multi-factor authentication for advanced security.
Keep SSH software updated 5.
Regularly update both the SSH client and server software. This ensures you benefit from the latest security patches and protections.
Enhancing your SSH security with these measures protects your Linux server from potential threats while allowing safe and efficient management.
Common SSH errors
Even with a correct setup, SSH connections can fail for several reasons. Understanding common errors helps you fix problems faster.
1. Permission denied (publickey)
This error appears when key authentication fails. It usually means the server cannot verify your public key.
Check that your public key is added to the Linux server. Confirm that file permissions are set correctly.
2. Connection timed out
This error occurs when the server does not respond. It can happen due to firewall rules or network issues.
Verify the server IP, SSH port and network connectivity. Ensure the SSH service is running on the server.
3. Host key verification failed
This error appears when the Linux server’s fingerprint has changed. It may indicate a legitimate change or a security risk.
Remove the old entry from the known hosts file. Then reconnect and accept the new fingerprint.
SSH cheat sheet
A cheat sheet lets you recall common commands without searching documentation. When working with SSH, it helps to have a quick reference.
Most common SSH commands
These are the commands you’ll use most often:
1. ssh username@server_ip
2. pwd
3. ls
4. cd /path
5. cp file1 file2
6. mv oldname newname
7. rm file.txt
8. grep "text" file.txt
9. ps aux
10. df -h
They cover basic navigation, file management, searching and system monitoring.
Quick examples
Here are three practical SSH use cases you’ll run into often:
1. Connect to a server and list website files
ssh [email protected]
ls -al /var/www
This connects to the Linux server and displays all files in the website directory.
2. Transfer a file to the server securely
scp backup.zip username@server_ip:/home/username/
This uploads a file from your local system to the server.
3. Check recent log entries on the server
tail /var/log/syslog
This shows the latest log entries for quick troubleshooting.
Final thoughts
SSH gives you secure, direct access to your Linux server, letting you manage files, transfer data, monitor performance and troubleshoot issues efficiently. Mastering a few essential commands can save time, simplify workflows and give you full control over your hosting environment.
With Bluehost, enabling SSH is easy. You can connect securely, run commands and manage your server without complex setup. Our built-in security, reliable performance and 24/7 expert support make it simple to focus on growing your website or application.
Take control of your Linux server today – enable SSH in your Bluehost dashboard and start managing your hosting like a pro. Explore Bluehost hosting plans now to combine secure server access with top-tier performance and support.
FAQs
What is SSH used for?
SSH is used to securely connect to remote servers, run commands, manage files and perform server tasks efficiently.
Is SSH safe to use?
Yes. SSH encrypts all communication between your computer and the server, protecting data from interception.
Do I need SSH keys to use SSH?
No. You can log in with a password, but SSH keys are more secure and recommended for long-term access.
What is the default SSH port?
The default port is 22. You can change it to enhance security and reduce exposure to automated attacks.
Why am I getting a “Permission denied (publickey)” error?
This usually happens if your public key isn’t added to the server or if file permissions are incorrect.
Do Bluehost plans support SSH access?
Yes. Most Bluehost hosting plans include SSH access, which can be enabled easily from your dashboard.


Write A Comment